Introduction
As technological defenses improve, cybercriminals are increasingly relying on social engineering techniques to exploit the weakest link in the security chain: people.
Social engineers employ a variety of techniques, both online and offline, to trick unsuspecting users into jeopardizing their security, transferring money, or disclosing sensitive information.
In 99% of cyberattacks, users are tricked into installing malware using social engineering techniques, according to Proofpoint's 2019 research, The Human Factor.
Social Engineering is recognized as one of the most effective ways to obtain information and break through a defense's walls. It is so effective because technical defenses (like firewalls and overall software security) have become substantially better at protecting against outside entities.
Social Engineering termed Human Hacking is mostly used for the recent attacks in the Web2 and Web 3 world mostly, attackers try to manipulate humans to divulge information or just a click to get access to the system. As easy as it might look, it is a very dangerous type of attack in the line of hacking.
What is Social Engineering?
Social Engineering in the context of Information Security is the psychological manipulation of humans to perform some actions or divulge valuable/confidential information.
Social engineering attacks are carried out in one or more steps. A perpetrator first investigates the intended victim to gather background information needed to carry out the attack, such as potential points of entry and weak security protocols.
The attacker then attempts to gain the victim's trust and provide stimuli for subsequent actions that violate security practices, such as disclosing sensitive information or granting access to critical resources.
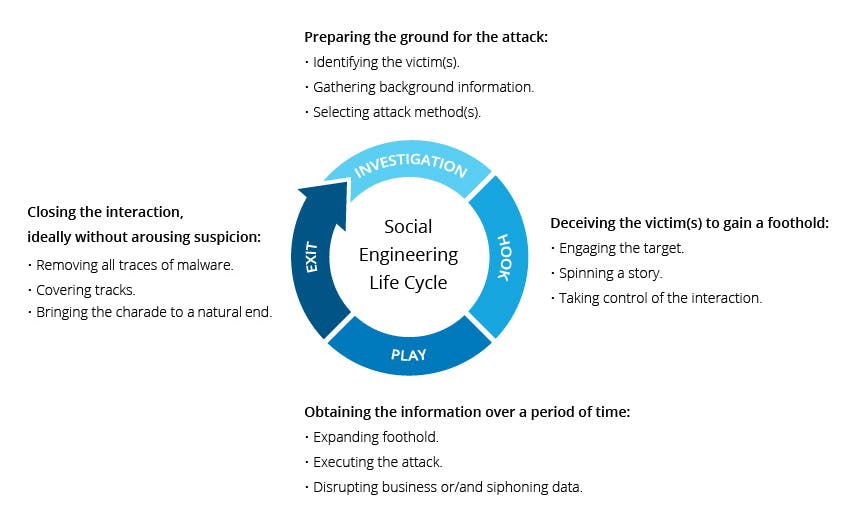
Lifecycle of a Social Engineering Attack
Social Engineering Techniques
Attacks using social engineering can be carried out anywhere there is a chance of human interaction. The five most typical types of digital social engineering attacks are listed below.
1. Phishing - Phishing scams, one of the most common forms of social engineering attack, are email and text message campaigns designed to make victims feel rushed, curious, or afraid. Then it prompts people to divulge private information, click on links to malicious websites, or open attachments that are infected with malware.
An illustration would be an email sent to subscribers of an online service informing them of a policy violation that necessitates quick action, like a necessary password change. It contains a link to a malicious website that looks almost exactly like its legitimate counterpart and asks the unsuspecting user to enter their current login information and a new password. The information is delivered to the attacker upon data entry.
Given that phishing attempts send nearly the same or identical messages to all users, mail servers with access to threat-sharing platforms find and block them significantly more quickly.
2. Spear Phishing - In this more specialized form of a phishing scam, the attacker picks certain people or companies to target. Then, in order to make their attack less obvious, they modify their communications based on the traits, positions held, and contacts of their victims.
Spear phishing is far more difficult to pull off and might take weeks or even months to complete. If done expertly, they're significantly more difficult to detect and have higher success rates.
An attacker could send an email to one or more employees while posing as an organization's IT consultant in a spear phishing scenario. It is written and signed exactly like the consultant would, leading recipients to believe it is an actual message.
Recipients of the mail are urged to update their passwords, and a link in the message sends them to a fraudulent page where the attacker can now steal their credentials.
3. Pretexting - Here, an attacker gathers data by telling a series of finely constructed lies. The con is frequently started by a perpetrator who poses as someone who needs the victim's private information to complete an essential factor.
The attacker typically begins by gaining the victim's trust by posing as a coworker, police officer, bank or tax official, or any person with the authority to know something. Through questioning that is apparently necessary to verify the victim's identification, the pretexter collects vital personal information.
This fraud is used to obtain all kinds of important data and records, including social security numbers, individual addresses and phone numbers, phone records, dates of staff vacation, bank records, and even security data pertaining to a physical plant.
4. Scareware - Scareware bombards victims with fake threats and false alarms. Users are tricked into believing their computer is infected with malware, which leads them to install software that either serves only to profit the attacker or is malware in and of itself. Other names for scareware include fraudware, deception software, and rogue scanner software. The legitimate-appearing popup ads that show in your browser as you browse the internet and contain language such as "Your computer may be infected with harmful spyware applications" are a frequent type of scareware. Either it offers to install the malicious tool for you or it sends you to a malicious website where your machine is infected.
Additionally, spam emails that provide false alerts or urge recipients to purchase useless or hazardous services are a common way for scareware to spread.
5. Baiting - As the word implies, baiting attacks use a fake promise to spark a victim's curiosity or sense of desire. In order to steal their personal information or infect their systems with malware, they trick users into falling into a trap.
The most despised type of baiting spreads malware using tangible media. Infected flash drives are frequently used as bait by attackers, who place them in clear view where potential victims are sure to see them (e.g., bathrooms, elevators, the parking lot of a targeted company). The lure has a legitimate appearance, including a label that presents it as the business's payroll list.
Out of curiosity, the victims pick up the bait and place it into their home or office computer, which causes the system to automatically download malware.
Baiting scam tactics don't always have to be played out in the real world only. Online baiting takes the form of attractive advertisements that direct visitors to harmful websites or drive them to download malware-laden software.
Preventing Social Engineering
Knowing the prevention of Social Engineering attacks can save you from falling victim to the attack. Moreover, the following tips can help improve your vigilance in relation to social engineering hacks.
1. Do not open emails or attachments from unknown senders - You are not required to respond to an email if you do not know the sender. Even if you know them and are suspicious of their message, double-check and confirm the information from other sources, such as by phone or directly from a service provider's website. Remember that email addresses are constantly spoofing; even an email purportedly from a trusted source could have been initiated by an attacker.
2. Use multifactor authentication - User credentials are one of the most valuable pieces of information that attackers seek. Using multifactor authentication helps to protect your account in the event of a system compromise.
3. Be cautious of enticing offers - If an offer sounds too good to be true, think twice before accepting it. You can quickly determine whether you're dealing with a legitimate offer or a trap by Googling the topic.
4. Update your antivirus/antimalware software - Check for automatic updates, or make it a habit to download the most recent signatures first thing each day. Check to ensure that the updates have been applied on a regular basis, and scan your system for potential infections.
Conclusion
Social Engineers use human emotions like curiosity and fear to their advantage in order to carry out their plans and lure victims into their traps. Therefore, exercise caution if you receive a worrying email, are drawn to an offer on a website, or come across errant digital media. You can defend yourself against the majority of social engineering attempts that occur online by being vigilant.
